Download Brute Force Password Cracker Facebook
A password is a mystery word or expression that is utilized for the verification procedure in different applications. It is utilized to access records and assets. A secret key shields our records or assets from unapproved get to. What is the Password Cracking?
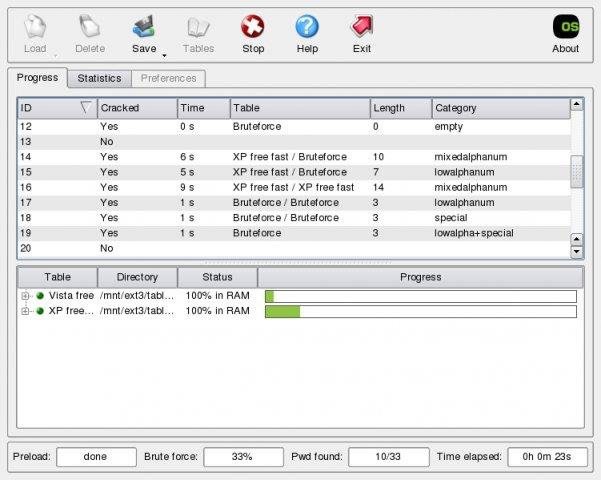
Sep 18, 2018 - 10 Most Popular Password Cracking Tools [Updated for 2018]. But, once the table is ready, it can crack a password must faster than brute force tools. You can download these tables and use for your password cracking. Download BruteForcer for free. A client-server multithreaded application for bruteforce cracking passwords. A simple password recovery tool written in.
Secret key breaking is the way of speculating or recuperating a password from putting away areas or from information transmission framework. It is utilized to get a secret word for unapproved gets to recuperate an overlooked password. In entrance testing, it is utilized to check the security of an application.
We found that Dojki-hd.ru is poorly ‘socialized’ in respect to any social network. Dojki-hd.ru is tracked by us since January, 2016. Over the time it has been ranked as high as 91 949 in the world, while most of its traffic comes from Russian Federation, where it reached as high as 6 565 position. It was hosted by OVH SAS, OVH HOSTING OY and others. Tosti na denj rozhdeniya na kirgizskom yazike. Dojki-hd has the lowest Google pagerank and bad results in terms of Yandex topical citation index.
As of late, PC software engineers have been endeavoring to guess the secret key in less time. The greater part of the secret is to log in with each conceivable blend of guess words.
On the off chance that the secret word is sufficiently solid with a blend of numbers, characters and uncommon characters, this breaking technique may take hours to weeks or months. A couple of secret key breaking devices utilize a word reference that contains passwords.
These apparatuses are absolutely subject to the word reference, so the success rate is lower. In a previous couple of years, software engineers have created numerous secret key to break the password. Each tool has its own favorite method. In this post, we are covering a couple of the most well-known password. What is Hydra? The Hydra is a quick system login password hacking tool.
When it is contrasted and other comparable devices, it demonstrates why it is speedier. New modules are anything but difficult to introduce in the instrument. You can without much of a stretch include modules and upgrade the highlights., Linux, Free BSD, Solaris and OS X. This instrument bolsters different system conventions. As of now it bolsters Asterisk, AFP, Cisco AAA, Cisco Auth, Cisco empower, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP, SOCKS5, SSH (v1 and v2), Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP How does Hydra work?